
As the world is changing rapidly, it is crucial to understand the new threats to data security.
For starters, you must know how to categorize sensitive and generic data. The former entails safeguarded information. It includes personal data of the employees and customers, their social security numbers, credit card details, etc. It has all the data required by an agency to meet payroll, fill urgent orders, or execute other business functions. Generic data, on the other hand, includes information with a limited chance of exploitation.
Disclosure of any sensitive information might result in loss of reputation, financial setback, civil or criminal penalties, etc. Indeed, it can be severely painful if data breaches of your company are plastered all over the papers.
The retail giant TJX had details of at least 45.6 million credit cards stolen by hackers who stole the information after cracking the data encryption system of the company.Later, the company faced severe criticism by the media for the lax standards of data security.
It all boils down to one fact – network security should be a priority for every business, regardless of its size. Below, we have outlinedfive security practices you can deploy to protect sensitive information:
1. Save little information
Nowadays, companies have revamped their engagement tactics. They believe that the more information they gather, the more is their chance to hold onto the customers. It has become a trend, and consumers do not hesitate to provide all personal details.
For the most part, they believe that businesses will use their information to deliver personalized products and services.
However, if their data gets into the wrong hands, the credibility of the company goes down the drain. Asimple solution to this problem is to save as little information as possible. This limits what hackers can steal.
You must only allow for information that is apt for your product/service. Avoid collecting anything extra. In case you require access to any additional details, make sure you wipe it off your servers properly after usage.
2. Educate employees at all levels
One of the leading causes that enable data breaches and hacks is human error. According to a survey conducted by the Ponemon Institute, employees account for 54% of data breaches, either through negligence or ignorance.
Large corporations make an effort to keep employees informed about internal cybersecurity policies and compliance regulations. They provide clear guidelines and train them accordingly. This training includes all kinds of interaction they might have with malicious files. It ensures that employees are vigilant of tactics like phishing emails, free file-sharing apps, etc.
3. Use encryption across the system
According to the IBM 2018 Cost of a Data Breach Study, it costs $3.86 million to recover from an average data breach. Encryption is one of the most secure features to protect sensitive information of your company.

If your business needs to collectpersonally identifiable information (PII) from the stakeholders, it is crucial to keep it secure. Encryption involves using algorithms to convert your data into unique and complex codes that are difficult to decipher.
There are different kinds of encryption methods you must know about. These include:
- Advanced Encryption Standard (AES)
- Rivest-Shamir-Adleman (RSA)
Before you opt for either method, it is vital to map out your needs first. A business must strive to achieve high-grade network security for its systems. A survey conducted in 2019 revealed that 45% of the companies claimed to have an encryption strategy in place to protect themselves from hackers.
4. Use multiple layers of security
Besides encryption, there are other security measures that a company must have in place. These steps provide the additional layer of security to your data.
You can go for spam filters to keep away from phishing scams and malware, or you can install a VPN like Cisco Anyconnect to secure your remote data connections. Having a VPN delivers multiple security services to protect an enterprise.
You can also go for a firewall. It will keep the criminals out and sensitive data within.According to Jack Wilson, the Vice President and General Manager of North America for Senucia, not having endpoint security is among the biggest corporation security threats.
He sheds light on how the business and private endpoints are soft targets for cybercriminals. It is the spot where most valuable data is present with the least protection.
5. Implement a BYOD Policy
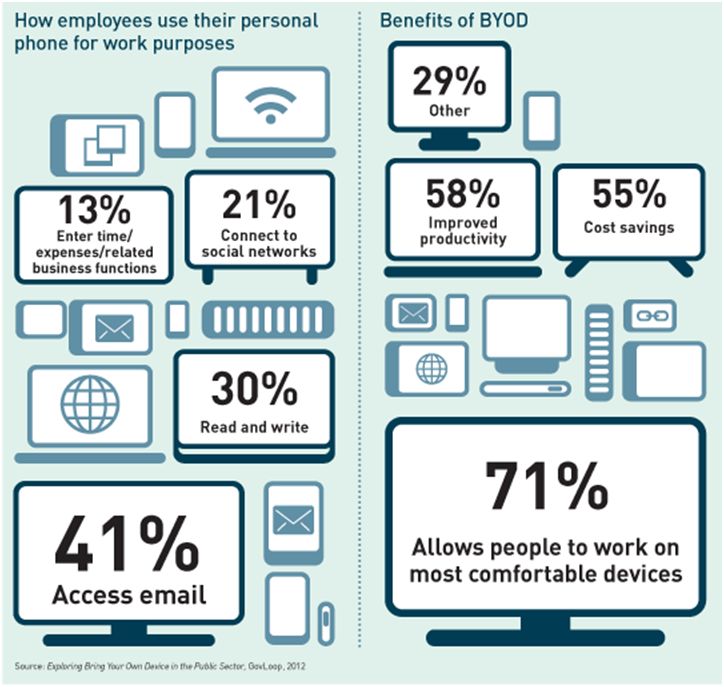
With the Bring Your Own Device (BYOD) trend gaining momentum, companies are allowing their employees to work from their devices and laptops. As this extends a company’s ability to achieve its targets, there are a few downsides they must tackle. For instance, an outdated operating system may cause data leakage.
A smart move would be to devise a strict BYOD policy. It means that employees must adhere to specific security measures when they use their device to access the company’s data.
It includes actions like software installation and configuration. Along with this, the company has to provide support for software updates, troubleshooting, and maintenance.
Accessing company information on personal devices means that data travels outside company confines. The business must have a highly optimized security system in place to make sure employees do not carry any private information outside (intentionally or unintentionally).
You can also go for tricks like segregating employee duties. This prevents any single employee from handling too much information.
A survey by Citrix Mobility reveals that 68% of employees access their files from their smartphones. This figure will continue to rise. The only way to make the practice of BYOD more secure is to implement strict penalties for faulty conduct.
Final thoughts
Not having adequate data security features has caused the failure of many small and medium-sized businesses. Even though you can’t eliminate the possibility of data breach or fraud completely, you can control its impact.
As we enter the age of data protection, you can steadily adopt policies for protecting sensitive information. There will be bumps on this road for sure. Yet, the key here is to be flexible. You must make efforts to upgrade your security features.
No one can sneak into your network if you stay high alert all the time.